Hilton Hotel | SydneyTuesday, February 25, 2025 | 8:00AM – 5:00PM
Link: https://register.paloaltonetworks.com/igniteontour-sydney-2025
Other Blogs from these events
Message:
I had the incredible opportunity to attend Palo Alto Networks: Ignite On Tour Sydney 2025, where I immersed myself in the latest advancements in cybersecurity. The event was truly inspiring, featuring insightful speakers and engaging discussions with industry experts.
I had the privilege of networking with Palo Alto Networks engineers, sales professionals, solution architects, and sponsors, gaining valuable insights into cutting-edge security solutions. This experience has further fueled my passion for protecting IT environments and safeguarding data from cyber threats.
Cybersecurity is not just a concern for businesses—everyone who uses the internet is a potential target. A single attack can lead to downtime, business disruptions, and even brand reputation damage. If you’re a business owner, CTO, or CEO—or if you know someone who might be interested—let’s connect. I’d be more than happy to help strengthen your security posture.
Are you prepared for the evolving cybersecurity landscape? Let’s take proactive steps together.
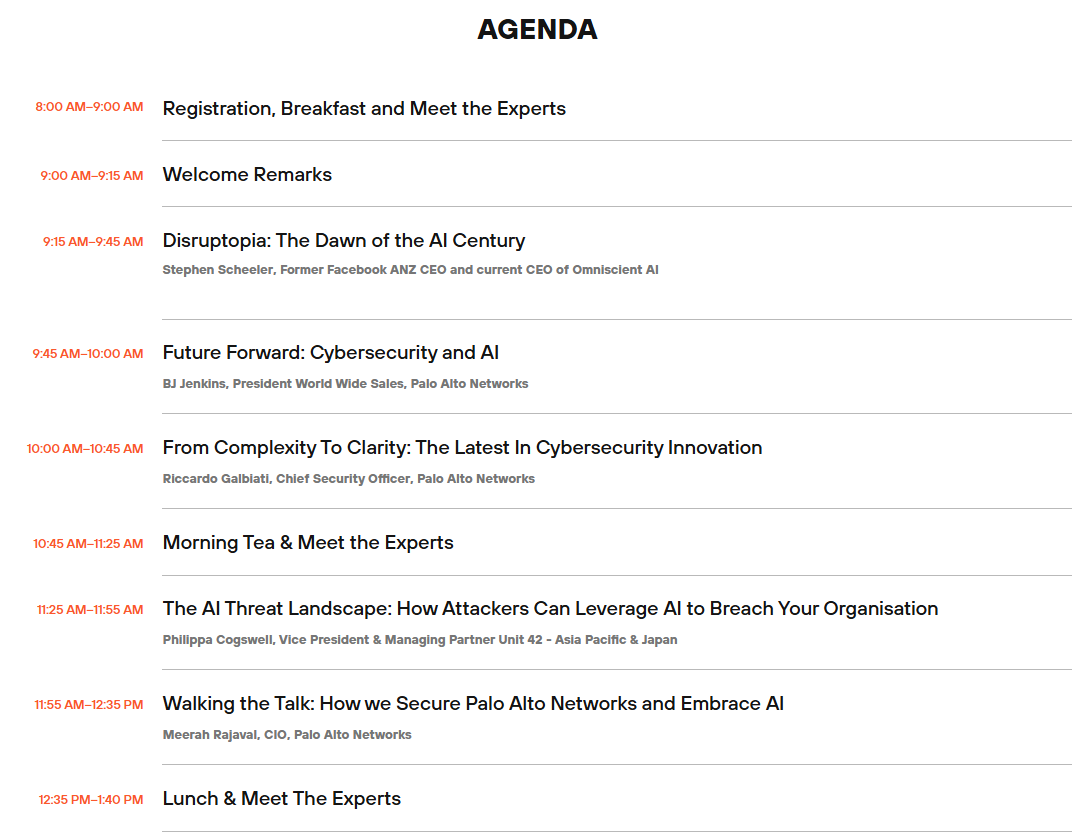
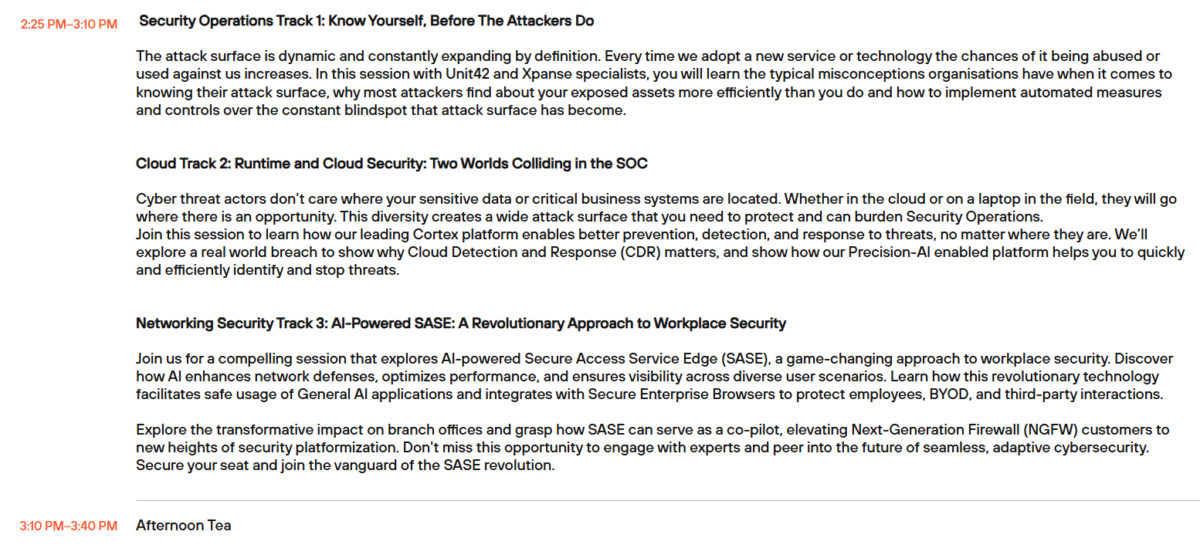
Event Agendas


Executive Summary
- Multi-Cloud Adoption & Security Challenges
- Enterprises are migrating to multi-cloud environments for agility, scalability, and AI-driven workloads.
- This expansion introduces complexity: inconsistent policies, diverse tech stacks, and siloed tools.
- Key Insights
- Fortune 500 Cloud Security Success
- Reduced accidental exposures by 56% using a centralized XSIAM solution.
- 850+ RDP/SSH misconfigurations remediated in minutes.
- 700K+ instances across AWS, GCP, Azure centrally managed.
- Fragmented Architecture
- Policies enforced at multiple points lead to disjointed security efforts.
- Each new technology often spins up separate infrastructure and security.
- GenAI Frenzy
- $270B+ invested in AI infrastructure in the past three years.
- 13× growth in open-source AI models since 2022.
- AI adoption in enterprises nearly doubled year-over-year (from 43% to 96%).
- AI Turbocharges Attacks
- Ransomware dwell time and data exfiltration windows shrinking from days/hours to mere minutes.
- Fortune 500 Cloud Security Success
- Platformization & Zero Trust
- A unified security platform (e.g., Strata Network Security + Cortex XSIAM) addresses fragmented environments.
- Zero trust network security, AI-driven SOC operations, and integrated cloud security drive better efficiency and protection.
- Recommendations
- Adopt Integrated AI-Powered Security: Automate detection, policy enforcement, and governance.
- Enforce Zero Trust: Apply least-privileged access across clouds, on-premises, and endpoints.
- Embrace Shift-Left (DevSecOps): Identify vulnerabilities in code before production deployment.
By leveraging an AI-enhanced, platform-based approach, organizations can unify multi-cloud security efforts, reduce manual errors, and proactively protect against evolving threats. Firms embracing platformization and AI-driven automation will see improved resilience, faster detection and response times, and stronger overall cybersecurity posture.
In-Depth Report
1. Introduction & Background
- Rise of Multi-Cloud Environments
- Driven by digital transformation and an urgency to support AI workloads at scale.
- Offers on-demand resources but broadens the attack surface.
- Security Complexity
- Fragmented Tools: Different teams often deploy standalone security solutions (firewalls, endpoint protection, etc.) without unified oversight.
- Policy Inconsistency: Each cloud provider (AWS, Azure, GCP) introduces unique settings, making consistent policy enforcement challenging.
- Human Error: Misconfigurations can lead to accidental exposures, as indicated by a 56% reduction once a centralized solution was used.
- Shift Toward Integration & AI
- Attackers leverage automation, shrinking the time from infiltration to exfiltration to minutes.
- AI-driven security helps organizations respond in kind, automating detection and remediation.
2. Key Insights from Live Session
2.1 Fortune 500 XSIAM Case Study
- Centralized Management
- Decrease in exposed instances by 56%.
- 850+ RDP/SSH vulnerabilities remedied in minutes.
- Over 700K instances managed seamlessly across AWS, GCP, Azure.
- Implication
- Demonstrates the power of real-time visibility and automated response at scale.
2.2 Fragmented Enterprise Networks
- Disjointed Policies
- Security often enforced differently in data centers, public cloud, SaaS apps, and remote endpoints.
- Increases operational overhead and risk of gaps.
- Overlapping Tech Stacks
- Different business units may use separate security solutions, hindering centralized governance.
- Impact
- Slower response times, complicated investigations, potential for unmonitored lateral movement.
2.3 AI’s Moral Alignment Gap
- “AI still misaligns with humans on moral reasoning”
- Tools can make unexpected decisions without ethical filters.
- Necessitates human oversight, ethical guidelines, and explainable AI frameworks.
2.4 GenAI Frenzy & Market Trends
- Significant Investment
- $270B in AI infrastructure in the last three years.
- Exploding Number of Language Models
- 13× increase in open-source AI models since 2022.
- Proliferation of Native AI Apps
- 2× growth in just 12 months; from 1.6K to 3K enterprise AI applications.
- Enterprise AI Usage
- Nearly doubled from 43% to 96% adoption, reflecting mainstream acceptance.
2.5 AI Turbocharging Cyber Attacks
- Ransomware
- Previously took ~12 hours to execute; now attackers can act within minutes.
- Compromise & Exfiltration
- Time to steal data collapsed from days to mere minutes.
- Vulnerability Exploits
- Once took weeks or months to weaponize; now can happen in less than an hour.
- Implication
- Security operations need AI-driven automation to match attackers’ speed.
2.6 Platformization & Zero Trust
- Zero Trust Network Security
- Ensures every request (user, device, workload) is authenticated and authorized continuously.
- AI-Driven SOC Operations
- Integrates SIEM, EDR, NDR, SOAR, and cloud security into a single data platform.
- End-to-End Cloud Security
- Monitors code-to-cloud and runtime environments in real time.
- Outcome
- Reduced complexity, consolidated data, stronger threat intelligence.
3. Evolution of Cloud Security
3.1 Early Cloud Posture Management (Circa 2019)
- Cloud-Native Application Protection (CNAPP)
- Combined CSPM (Cloud Security Posture Management) and CWPP (Cloud Workload Protection Platform).
- Provided basic hygiene checks for misconfigurations, compliance, and best practices.
- Shortcomings
- Often reactive; found issues but lacked real-time threat response.
3.2 Shift-Left Security & DevSecOps (Circa 2021)
- Code-to-Cloud Security
- Integrated security scanning early in development pipelines (IaC, containers, microservices).
- Reduced last-minute patching by catching vulnerabilities prior to production.
- Bridgecrew Acquisition
- Helped automate scanning of IaC templates, ensuring misconfigurations are fixed before deployment.
- Remaining Gaps
- Siloed data from dev to production.
- Only partial automation for certain threat scenarios.
3.3 Cloud Detection & Response (Circa 2024)
- Real-Time Monitoring
- 7M+ security agents across containers, serverless, and VM-based workloads.
- Proactive Defense
- Automated correlation of logs and alerts, letting AI weed out false positives.
- AI-based anomaly detection quickly flags unusual activity, halting potential breaches.
- SOC Integration
- Tools like Cortex XSIAM unify SIEM, SOAR, EDR, NDR, and CSPM data for a 360° view.
- Reduces mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR) significantly.
4. Strata Network Security Platform: Precision AI™
- Core Offerings
- Unified Policy Management: Single console for on-prem, cloud, IoT, remote workers.
- Precision AI™: Machine learning models trained on vast telemetry to detect anomalous behaviors.
- Key Differentiators
- Holistic Visibility: All network traffic is analyzed and correlated in real time.
- Dynamic Access Control: Aligns with zero trust principles—granting minimal privileges.
- Reduced Operational Overhead: Fewer disjointed tools, less manual policy syncing.
- Business Value
- Faster compliance, simplified governance, lower overall cost of ownership.
5. AI as a Security Game-Changer
5.1 AI-Driven Productivity Gains
- AI-Generated Code
- Reduces repetitive tasks, such as encryption scripts, infrastructure automation, and code linting.
- Accelerates release cycles while maintaining security best practices.
- AI-Created Content
- Automates creation of marketing materials, documentation, user guides.
- Frees knowledge workers to focus on strategy rather than rote writing.
- AI-Powered Support
- Self-service chatbots for L1 troubleshooting, password resets, system diagnostics.
- Identifies frequent issues and auto-remediates them before user tickets are filed.
5.2 AI-Driven SOC Operations
- Cortex XSIAM
- Data Correlation: Aggregates logs from various sources (firewalls, endpoints, cloud).
- Automated Detection: 7,000+ specialized AI detectors scan data for threats like lateral movement, domain abuse, or malicious insiders.
- Playbook-Driven Response: 1,000+ automated workflows that handle phishing campaigns, malware outbreaks, misconfigurations, etc.
- Reduced MTTR/MTTD
- AI quickly triages and escalates genuine issues to analysts.
- Human teams can focus on advanced threats, investigation, and policymaking.
5.3 Ethical & Governance Considerations
- AI Misalignment
- AI could make decisions misaligned with human ethics or privacy regulations.
- Organizations must establish ethical guidelines and maintain human “kill switches.”
- Regulatory Compliance
- Evolving standards like the EU AI Act, GDPR, and industry-specific guidelines (HIPAA, PCI-DSS) demand robust data governance.
- Zero Trust & Policy Controls
- AI modules themselves should be restricted in scope, with logs and audits to trace AI-generated actions.
6. Future Outlook & Strategic Recommendations
6.1 AI-Enhanced Threat Prediction
- Proactive Defense
- Moving from signature-based detection to predictive analysis, leveraging global threat intelligence and local environment baselines.
- Adaptive Policies
- AI can dynamically adjust firewall rules or micro-segmentation based on real-time threat intel.
6.2 SASE & Zero Trust Convergence
- Secure Access Service Edge (SASE)
- Merges SD-WAN with CASB, FWaaS, ZTNA for comprehensive cloud-delivered security.
- Consistent Policy Enforcement
- All endpoints (remote workers, IoT, SaaS) governed uniformly, reducing security gaps.
6.3 AI-Assisted DevSecOps
- Continuous Code Scanning
- AI integrated with CI/CD tools to detect vulnerabilities in real time.
- Automated patching or recommended fixes expedite secure releases.
- Shift-Left Acceleration
- Embedding security from design phases reduces risk in production.
6.4 Platformization Imperative
- Unified Console & Data
- Eliminates duplicative solutions, streamlines alerts, fosters shared threat intelligence.
- Key Benefits
- Faster resolution, better resource allocation, enhanced ROI on security spend.
7. Step-by-Step Implementation Roadmap
- Audit Current State
- Inventory existing tools, policies, and cloud usage.
- Identify overlaps and gaps in coverage.
- Consolidate & Integrate
- Transition to a unified platform (e.g., Strata + Cortex XSIAM).
- Centralize logs and policies for holistic visibility.
- Adopt Zero Trust
- Implement micro-segmentation, continuous verification for every user/device.
- Grant least-privileged access, monitored and revoked when risk arises.
- Shift-Left & DevSecOps
- Embed security scanning in CI/CD, apply code analysis and IaC checks.
- Standardize best practices for container security and microservices.
- Leverage AI & Automation
- Configure AI-driven playbooks for common threat scenarios (phishing, malware, misconfig).
- Use anomaly detection to proactively spot insider threats or data exfiltration attempts.
- Foster a Security Culture
- Train staff on AI ethics, data protection, and agile security practices.
- Encourage DevOps and security teams to collaborate continuously.
- Measure & Refine
- Track KPIs (MTTD, MTTR, false positives, vulnerability dwell time).
- Regularly update AI models and policies to adapt to new threats.
8. Conclusion
- Convergence of Cloud, AI & Security
- As AI workloads grow, attack surfaces expand, demanding integrated, real-time security.
- The answer lies in platforms that unify posture management, AI-driven threat detection, and automated response.
- Key Takeaways
- Platformization minimizes silos, reduces administrative overhead.
- Zero Trust ensures continuous verification, drastically cutting insider and external risk.
- Shift-Left fosters early vulnerability detection, preventing production exploits.
- AI-Driven SOC compresses detection and response timelines to match attacker speed.
- Call to Action
- Move beyond standalone security products to a cohesive, AI-enabled ecosystem.
- Implement governance structures to ensure AI remains ethical, compliant, and transparent.
- Continuously iterate: security must evolve with shifting technologies and threat vectors.
By prioritizing an integrated, AI-driven approach to multi-cloud security, enterprises can future-proof their defenses, maintain compliance, and unlock the full benefits of digital transformation.
References
- Live session images and presentations from the “Networking Security Track 3: The Future of Work is Web Centric” event
- Additional Data Sources & URLs
- Palo Alto Networks: Cortex XSIAMhttps://www.paloaltonetworks.com/cortex/cortex-xsiam
- Palo Alto Networks: Strata Network Securityhttps://www.paloaltonetworks.com/network-security
- Gartner “Market Guide for Cloud Workload Protection Platforms” (2023)https://www.gartner.com/en
- Forrester “The State of Zero Trust Security Strategies” (2022)https://www.forrester.com
- NIST SP 800-207: Zero Trust Architecturehttps://csrc.nist.gov/publications/detail/sp/800-207/final
- Stanford’s HAI AI Index Reporthttps://aiindex.stanford.edu/
Speakers and Event Sponsors

Meerah Rajavel
Chief Information Officer
Palo Alto Networks

BJ Jenkins
President WorldWide Sales
Palo Alto Networks

Riccardo Galbiati
Chief Security Officer
Palo Alto Networks

Philippa Cogswell
Managing Partner, Unit 42,
Asia Pacific & Japan
Palo Alto Networks

Steve Manley
Vice President, ANZ
Palo Alto Networks

Stephen Scheeler
CEO, Omniscient A
Former CEO, Facebook ANZ
Omniscient AI